Preface
Unfortunately FC has a family issue, one we all face in our lives. He and his wife are in the UK for that. We wish them the best of strength. His email came in after midnight. Given we were all meeting that day, we decided to discuss the analysis of the SKT hack published on the 4th July, that Dmitry covered so well in his Linkedin post.
We will have a session with FC once he has time and focus available. I’ll let you know when that is, as soon as I do.
SKT Background
Dmitry provided a background to the main findings of the SKT hack. On the numbers the revenue loss was $600M, and going forward SKT plans to spend $500m on security over 5 years, which likely doubles the security team. The loss of customers is current 800,000 having left at of the end of June from the breach announcement at the end of April.
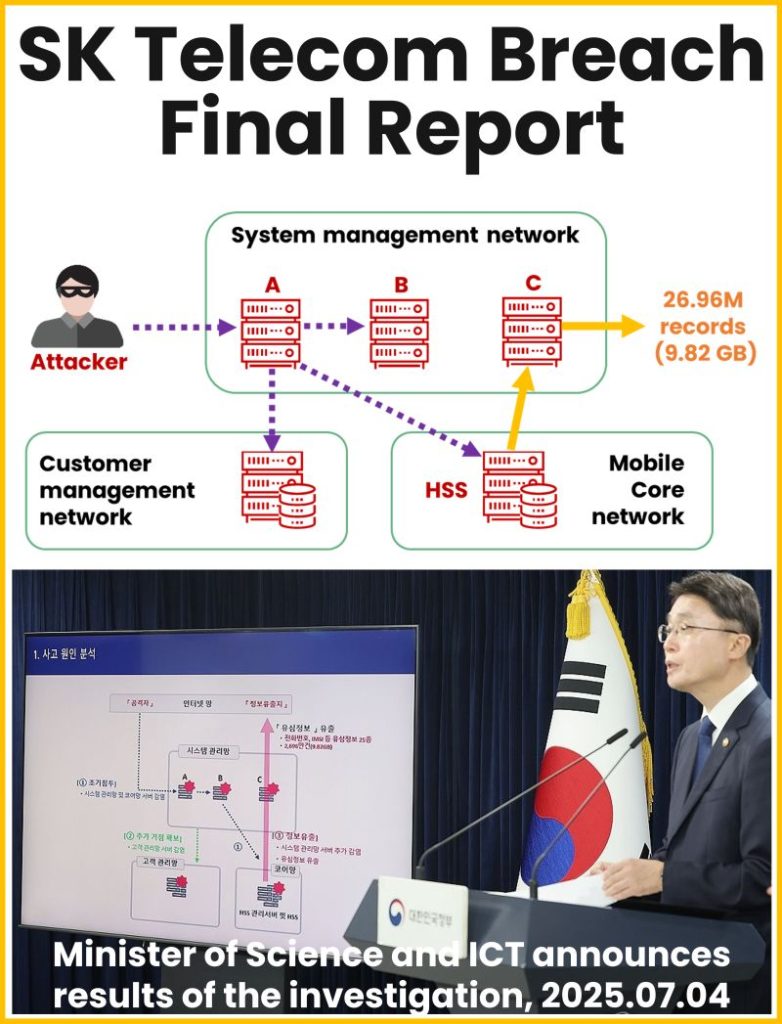
The hack began in August 2021, with a system management server being hacked. There were warnings from anomalous behavior, e.g. reboots, but no reports were generated / circulated to the regulator. From this breach internal systems were accessed using plain text.
In all, 33 different malware were found, including BPFDoor, CrossC2, and TinyShell. Then on April 2025 10GB of customer data was downloaded, including IMSI and USIM data, likely all the customers’ data.
The situation is symptomatic of the usual network and IT security issues in telcos. That is, the network gets all the funding and security survives on the scraps with limited tolerance of the protections and pentesting they recommend. An important point raised is unless security is a board level issue, funding and authority will remain a problem.
My recommendation is drop the Chief Transformation Officer. Their role appears to be maintaining spend with legacy vendors, I do not know how that leads to transformation. Instead have a CSO (Chief Security Officer) with a modern strategy that recognizes the organization will be hacked in the future, the skill is minimizing the impact.
A quote from the CISO from a major telecom group: “If cybersecurity isn’t a board-level concern, it won’t get the budget, the ownership, or the priority it needs. And this isn’t just a telecom issue – it applies to any large organization… and to smaller ones too.”
Voice AI Security Session Next Week
Coming up next week we have Cybersecurity Training in the Age of Voice AI from Enrico Faccioli, CEO & Co-founder at vishr.ai // seedata.io. That is using Voice AI to train staff through live hacking attempts. The best learning is through failure, as then you never forget.
AI-powered voice attacks are surging, with vishing (voice phishing) attempts increasing 442% in the latter half of 2024. Criminals can now clone the voice of a CEO to demand a wire transfer, making the threat more persuasive than ever. Meanwhile, traditional security training – with its generic videos and quizzes – is stuck in the past, creating a “checkbox culture” where learning lacks depth and is quickly forgotten.
Test your organization against realistic voice threats. Personalized, 1-on-1 AI voice coaching can replace passive videos, building true resilience by letting employees learn through conversation. This type of testing is becoming critical to keep people, processes, and technologies as effective as possible.
The Importance of A Diversity of Experts
Back to the discussion with Aaron Birnbaum, Bohdan Hopanchuk, Dmitry Kurbatov, and Jack Sessions. A strength of TADSummit is the diversity of people we bring to topics. Many of the old-boys events are so square, there is no daylight between the people. It’s a telco centric view, 20 years out of date because they do not engage the web-folk.
Dmitry
Dimitry highlighted the 4 years from hack to public exposure (2021-2025) shows there are process issues, not just a lack of funding. The procedures are not connected, e.g. the anomalous behavior of a server rebooting did not connect with further actions and investigations. The NIST Cybersecurity framework is not difficult, the challenge is implementation at scale.
Jack
Jack also mentioned the hack suffered by Optus in Australia, that started at 8M people, and expanded to 26 million. Yes, Jack was in Melbourne Australia during the call, 1-2AM his time. Thank you Jack.
Jack highlighted 3 underlying issues: The malware was quite simple, you do not need to be an expert, general software skills. Couple that with AI, and it drastically lowers the barrier to attacks. Jack referenced a presentation from FC on good and bad AI. AI has accelerated the creation of a effective phishing emails from 30 hours to one minute. And the attacks are being used in new ways that do not trigger the emails filters. Email remains the most popular delivery method, however RCS is being experimented with.
Jack highlighted for me a point I’d not fully appreciated, that of culture. Security engineers are encouraged to focus on writing reports, not the technical aspects. For example a threat hunter not working on the creation and detection of threats, rather writing reports on discovered threats. The cost of a data breach is only known after the fact, which makes the investment in protection against a breach tough. This reminded me of the issue I bought up for the challenge dev evangelists face in telcos “TADHack 2025. Why does Telecoms Service Innovation feel like an Oxymoron? Because the Web won, and telecoms has not caught up!“
In the security domain, they tackle the culture issue by focusing on mitigating the impact of a breach, than trying to stop all breaches.
Jack’s final point was on respect for your people, your customers, your organization in protecting them from cybercrime, and also respect for the your adversaries for their ingenuity to break into your systems.
Aaron
Aaron backed up that culture issue. Culture is across the organization, it’s not just software tools, its physical security as well. And it must come from the top, it’s not an after the fact bolt-on. Its at the start in the design of the systems and organization both physically and virtually. Regardless of design, people will click on inappropriate links. We’ve discussed this before on bring positively suspicious, as covered in our Telecom Cybersecurity session with Dmitry.
Aaron highlighted the importance to target the vector: email, voice, RCS; as well as the endpoint. Jack and Aaron had a fun discussion on quantum-safe. Which led to the importance of training people / agents, and protecting vectors, e.g. filtering all links in email. Dmitry made a great point, make the tools simple. Aaron then breaks into his quantum safe story 🙂
Bohdan
Bohdan focused the discussion onto the simple steps any enterprise can do. Try to hack your business, use well known social engineering hacks with publicly known information about your company, see if current systems and processes are adequate. Dmitry asked about a recent North Korean hack, and Bohdan countered with “Chinese also”, as using/blaming North Korea is a popular pastime of Chinese hackers.
Bohdan highlighted the risk of CPaaS platforms being hacked, like we saw with Syniverse. Which gives access to SMPP, HTTP, SS7, customer and partner databases, live traffic dashboards; security information like OTPs (One Time Passcodes) on well known short codes. The content of conversations both voice and messaging. Bohdan also mentioned a phone built by an African student that did not require a SIM or airtime, described here, that is not a threat. The CPaaS hacking is a much greater concern.
Dmitry mentioned the O2 Virgin VoLTE leaks, the setup allowed location and data disclosure. You can read more here.
Some Departing Bullets
We covered much, as always, leaving you with a few bullets.
- SKT report is a great case study and shows budgetary security figures.
- The cost of a data breach is only known after the fact, which makes the investment in protection against a breach tough. Its perceived as a cost center.
- Security must be a board level issue, it’s not a blot-on, its by design from the beginning.
- The SKT story shows the hack started in 2021 and the slow visible drift until the breach of all customer data in 2025.
- Bug bounties matter, a few $k could save you millions.