Firstly, thank you to STROLID for sponsoring both TADHack and TADSummit. I’m covering 2 presentations in this blog:
- SPONSOR KEYNOTE The Rise and Rise of vCon. Thomas McCarthy-Howe, CTO STROLID, Innovating Automotive Conversations. Thomas’s presentation slides.
- SCITT and vCon AI governance for conversations, at scale. Steve Lasker, Director of Ecosystem DataTrails. Steve’s presentation slides.
TADSummit was where vCon got its first public exposure, as Thomas explains, its vCon’s nest. This is an interesting keynote as Thomas reviews the steps in vCon’s development since 2021. STROLID Keynote, vCons: A Proposal for an Open Standard for Conversation Data was all the way back in 2021, while we were still social distancing.
We must give a shout out to Dan Petrie, the co-author of the vCon standard, He’s been there since the beginning of vCon.
The home of vCon is STROLID, they’re the sponsor of the project. STROLID helps people purchase cars, by listening to customers / leads. vCons help STROLID listen at scale, amongst many other things.
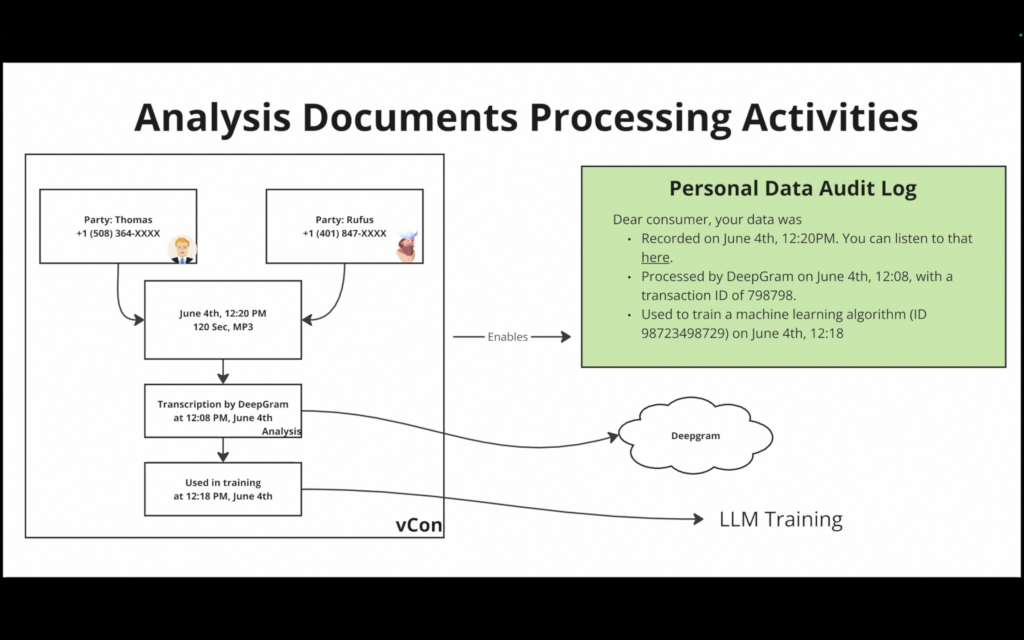
When vCon began, the components of the file type included: the conversation (audio / video / time and date), identities of people and agents in the conversation, analysis (mood, speech to text), and attachments (documents and presentations discussed and shown).
Along with the vCon whitepaper we made the case for containerizing conversations. With a group of experts, identified in the whitepaper, we developed the idea. In particular, vCon’s role in digital rights and governance, see diagram below. And with the support of the IETF, the vCon standard began.
An important aspect of standards bodies is all the related standards being created around the same time. This lead to the discover of SCITT (Supply Chain Integrity, Transparency and Trust). We have a great introduction from Steve Lasker to SCITT in Podcast 85: TADSummit Innovators, Steve Lasker, DataTrails.
Critically SCITT enables right to know and right to erasure. Auditors and regulators can know the personal data contained in a vCon. Personal data within an enterprise can be managed. And fakes exposed.
The explosion of LLMs, trained on many sources of data, became a driving use case for vCon adoption. Yet another data point on the rise and rise of vCon.
STROLID GPT provides a great real-world example of how vCon can be used to understand your business. Not just specific content, rather broader questions about the trends in the business, e.g. who has been test driving cars, and progressed to a sale.
We’re moving into a phase where vCon is maturing as new applications are found, e.g. discovering gaps in the customer record, so when that customer calls in, a few questions can be asked to fill out the record.
We’re now seeing privacy primers for developers of vCon. At TADHack we had a great hack “The Shrine at the Temple of Computing” by Jared Ashcraft and David Sikes. You can see all the other TADHacks here, vCon is a powerful file type.
Next we moved onto SCITT and vCon AI governance for conversations, at scale. Steve Lasker, Director of Ecosystem DataTrails.
Steve made a simple yet powerful point. Differentiating fiction from reality is getting harder. Trust of the information we consume is one of the greatest problems we face. We need SCITT (Supply Chain Integrity, Transparency and Trust) now. The volume of information is growing exponentially, we need to be able to automate trust at scale. Like vCon automates listening at scale.
The core of SCITT is, “who made an immutable statement about an artefact, at a specific point in time.” Now that ‘who’ can have a large variation in signal to noise ratio, it’s not just people, it’s also things, anything with an identity. Time is important as opinions and knowledge change, so when was the statement made matters; what was the statement; and what was the artefact, e.g. software (SBOM, Software Bill of Materials), vCon, or digital media.
The information is stored in Concise Binary Object Representation (CBOR), a data format designed for small code size and small message size. Basic security services defined for this data format are defined in CBOR Object Signing and Encryption (COSE) protocol This specification describes how to create and process signatures, message authentication codes, and encryption using CBOR for serialization. This specification additionally describes how to represent cryptographic keys using CBOR.
The data is notarized by for example DataTrails, who used SCITT to create a complete solutions, and a receipt issued. Steve then reviews the format of the SCITT envelope, and how given some vCons can be large, GB of data, the content of the vCon can be referenced.
Steve then walks through a STROLID use case. A member of the STROLID dealer network calls a customer (Gavin), the telco creates a vCon and sends it to the Data Controller, vConGPT.
Steve explains how consent is made possible and the lifetime for that consent. Consents and revoking consent for communications are receipted to Gavin.
Strolid the data processor, takes the vCon and performs actions such as sentiment analysis and transcription. Watch the video, from 33:00, it captures how powerful vCon and SCITT are for managing one of the biggest headaches in calling customers, consent. And for ensuring consistency in the data so everyone has the latest vCon for that conversation. For example, Gavin may revoke consent, so there needs to be redactions.
Steve then explains how PII (Personal Identifiable Information) is managed in an immutable ledger. There is no PII in the SCITT, however DataTrails has an evidentiary data store, where PII can be masked (essentially forgotten). The PII does reside in the vCon, and Gavin can revoke consent at any time. And that change is captured on the SCITT for that vCon.
We then break into a discussion with Sebastian Schumann, Deutsche Telekom, as he discovered how advanced vCon has become with SCITT. Check out Sebastian’s TADHack using vCon, Global Carrier vCon extension. Showing how easy it is to add vCon to a carrier’s CPaaS.


3 thoughts on “Sponsor Keynote. The Rise and Rise of vCon, Thomas Howe. + SCITT and vCon AI governance for conversations, at scale. Steve Lasker.”
Comments are closed.